- Home
- Technologies
- Self-Recognition Flows
Self-Recognition Flows (SRFs)
Most of the commercial Intrusion Detection Systems (IDS) and Intrusion Protection Systems (IPS) use a standard data structure such as Netflow (adopted by Cisco) [2] and/or Sflow (adopted by Juniper and other network vendors) to model the operations of end-to-end network connections and they use this data structure to detect network attacks. In our previous research, we have developed a new data structure that we refer to as Application Flow (AppFlow) to model the operations of protocols and applications and have used it to detect any anomalous event triggered by either a fault (hardware or software failures) or cyber-attacks [1, 3].
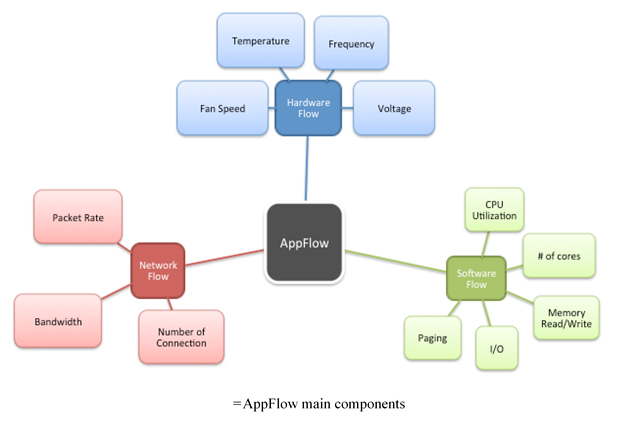
AppFlow is developed at the NSF Center for Cloud and Autonomic Computing (CAC) and also being commercially used by AVIRTEK, Inc (www.avirtek.com, a cybersecurity startup from the CAC center). AppFlow can be viewed as an n-dimensional array of features that capture temporal and spatial behaviors of communications protocols as well as applications, and characterize their dynamic interactions with respect to key hardware, software, and networks features (see Figure 3).
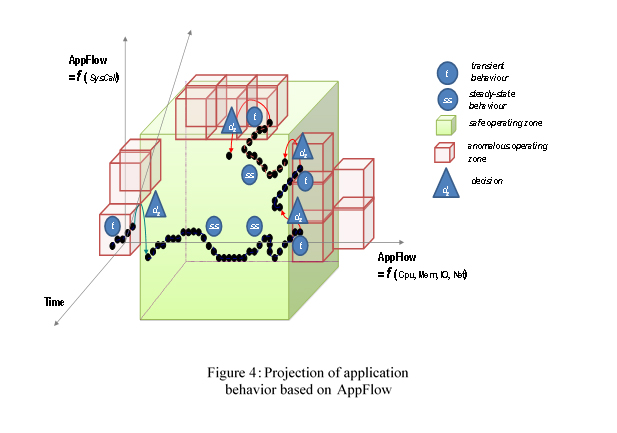
The AppFlow-based behavior analysis uses statistical and data mining techniques to determine the current operating region of the application and also projects its behavior in the near future. The operating point (OP) of an application can be defined as a point in an n-dimensional space with respect to well-defined attributes. An acceptable operating zone for an application can be defined by combining the normal operating values for each attribute. At runtime, the OP of an application moves from one zone to another and that point might move to a region where the application does not meet its security requirements. For example, the AppFlow (black dotted curve in Figure 4) moves outside the green sub-cube due to a software failure or cyberattack. By continuously monitoring the operating point of an application and using statistical and data mining techniques to project the trend of the operating point in the near future, we can proactively predict and detect the anomalous behaviors that might have been caused by malicious attacks. Furthermore, once it is determined that the application operating point is moving outside the normal region, it will consult a decision support system to determine the appropriate proactive management policy that brings the application behavior back into a normal operating region.
We have used AppFlow to predict the behavior of a multi-tier web-based ecommerce application that implements ecommerce transactions based on the TPC-W benchmark [1]. We have also used the AppFlow based anomaly behavior analysis to detect attacks against DNS, TCP, WiFi, and Modbus protocols [1, 3, 4, 5, 6, 7]. AVIRTEK has extended the AppFlow concept to develop novel data structures Cyber-Footprints that can model the users, physical and logical resources. Figure 5 shows an example of a User Cyber Footprint (UCF) data structure.